A honeypot field is an essential tool for developers aiming to enhance spam prevention in web forms, effectively keeping unwanted submissions at bay without relying on disruptive methods like reCAPTCHA. In today’s digital world, where bots are increasingly adept at avoiding detection, correctly implementing a honeypot field can significantly bolster form security. By cleverly disguising this hidden field, developers can trick spambots into revealing themselves, ensuring a more genuine interaction from real users. Utilizing robust bot detection techniques alongside a well-configured honeypot can help maintain the integrity of your data submissions. Whether you’re working with JavaScript forms or other frameworks, understanding the best practices for honeypot implementation is crucial in staying ahead of malicious activities.
In the realm of web development, a deceptive form field, often referred to as a decoy field, plays a pivotal role in curbing unwanted spam submissions. This deceptive mechanism allows developers to effectively shield their form inputs without resorting to intrusive methods. As spam bots continue to evolve, deploying this hidden trap not only enhances overall security, it also ensures that legitimate users experience a seamless interaction. By integrating advanced detection strategies and shaping the design of your decoy field, you create an environment where user engagement thrives while minimizing the chances of improper entries. Employing these innovative strategies can greatly elevate your form’s efficacy and security.

Understanding Honeypot Fields
Honeypots serve as a clever tool in the fight against spam submissions on websites. As of 2025, they remain an effective alternative to more intrusive measures such as reCAPTCHA. Essentially, a honeypot field is designed as a trap; legitimate users won’t interact with it, while automated bots often will. This distinction allows developers to filter out the spam easily and maintain the integrity of web forms.
To implement a working honeypot, developers must strategically design it to avoid detection by savvy bots. It’s not just about creating a hidden input field anymore; there are specific tricks and techniques needed to ensure that your honeypot remains effective amid increasingly sophisticated spamming tactics.
Implementing Honeypot Components
To utilize honeypots effectively, I’ve developed a Honeypot component that simplifies its implementation. By importing it into your project, you can easily integrate this feature without cumbersome code. For instance, in a Svelte application, include the script and add the Honeypot component as follows:
“`javascript
import { Honeypot } from ‘@splendidlabz/svelte’
“`
This straightforward approach reduces complexity, allowing you to focus on the form’s functionality rather than the hassle of creating anti-spam measures.
Avoiding Common Mistakes with Honeypots
When setting up a honeypot, awareness of pitfalls is crucial. For example, using “ or hiding fields with inline CSS can lead to failure, as modern bots are designed to recognize these methods as traps. Instead, using a visible text field that is styled to be hidden with non-inline CSS is much more effective. A basic implementation might look like this:
“`html
.honeypot { display: none; }
“`
This method cleverly conceals the honeypot from users while maintaining its trap function for bots.
Enhancements for Better Effectiveness
You may come across enhancements like `aria-hidden` and `autocomplete=off` to protect the honeypot further. However, it’s essential to understand that such additions might not be necessary if `display: none` is already in place. The effectiveness of a honeypot relies more on its deceptive nature than on unnecessary attributes.
When implementing enhancements, focus on plausible field names and better CSS class identifiers that don’t scream ‘honeypot.’ For example, using class names like `.form-helper` can obscure the field’s true purpose.
Preparing for Future Challenges
As bots continue to evolve, the strategies for detecting them must also adapt. Future-proofing your honeypot involves employing less obvious naming conventions for your attributes and hiding styling in separate CSS files. This method keeps the honeypot disguised, making it more resilient against newer scraping technologies.
For example, instead of naming the honeypot field ‘spam’, consider using benign names like ‘occupation’ or ‘website’. Pairing this with a decoy class name can further blur the lines for bots that may try to flag these elements.
Advanced Anti-Spam Techniques
Implementing general form checks can significantly reduce the likelihood of spam submissions. These checks come into play in various forms, such as ensuring user interaction through events like mouse or keyboard activity. Here’s how you can incorporate a Form component that uses your Honeypot effectively with the inclusion of JavaScript to monitor user actions:
“`javascript
import { Form, Honeypot } from ‘@splendidlabz/svelte’;
“`
Creating Intuitive User Interfaces
I’m excited to announce an upcoming project aimed at simplifying HTML form functionalities. My goal is to design a user interface that is not only intuitive but also maintains a high standard of accessibility. Features will include essential form elements like inputs, text areas, and buttons, all while incorporating honeypots seamlessly into the design.
The development of this user-friendly form system is driven by the need for developers to create more efficient forms while effectively combating spam. Stay tuned for updates as I will be sharing more details soon!
Recapping the Essentials of Honeypots
In sum, honeypots can significantly enhance your form’s capability to thwart spam if implemented correctly. The key lies in disguising these fields so that bots perceive them as legitimate. By mastering these techniques and staying ahead of evolving bot strategies, you can maintain the integrity of your web submissions.
This exploration into honeypots aims to equip you with useful insights to apply in real-world scenarios. Whether you choose to implement these techniques or explore other methods, understanding these principles is vital for maintaining effective spam protection.
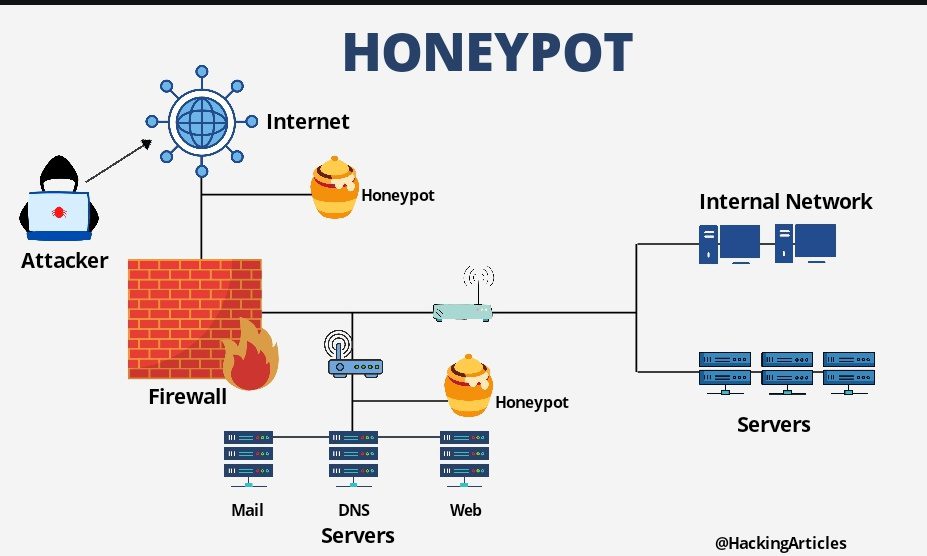
Conclusion
In conclusion, the use of honeypots remains a highly effective strategy for combating spam submissions in 2025. By incorporating a subtle yet clever design approach, developers can successfully implement honeypots that avoid detection by bots while maintaining user experience. It’s essential to not only use creative naming conventions and external CSS but also to actively engage with interaction detection techniques to enhance security further. Remember the following key points when implementing a honeypot:
– Use text fields with often overlooked names that bots won’t recognize as a trap.
– Avoid using common methods such as hidden input fields, which are easily detected by sophisticated bots.
In order to modernize your forms and keep spam at bay, consider all the discussed methods and available tools. By leveraging JavaScript to monitor user interaction or utilizing integrated components like the Splendid Labz Form solution, developers can create a seamless experience that minimizes the risk of unwanted submissions. The fusion of usability and security is vital—as spam detection evolves, so too must our strategies. To summarize:
– Employ interaction validation mechanisms to ensure genuine user engagement.
– Regularly review and adapt your anti-spam methods in accordance with emerging practices.